So, you have heard of hashing—a fundamental concept in cybersecurity and data management—but want to understand more? This article will cover why hashing is crucial, its core principles, types of hash functions, important guidelines for algorithm selection, and techniques to enhance hash security.
So, let’s get started!
What is Hashing?
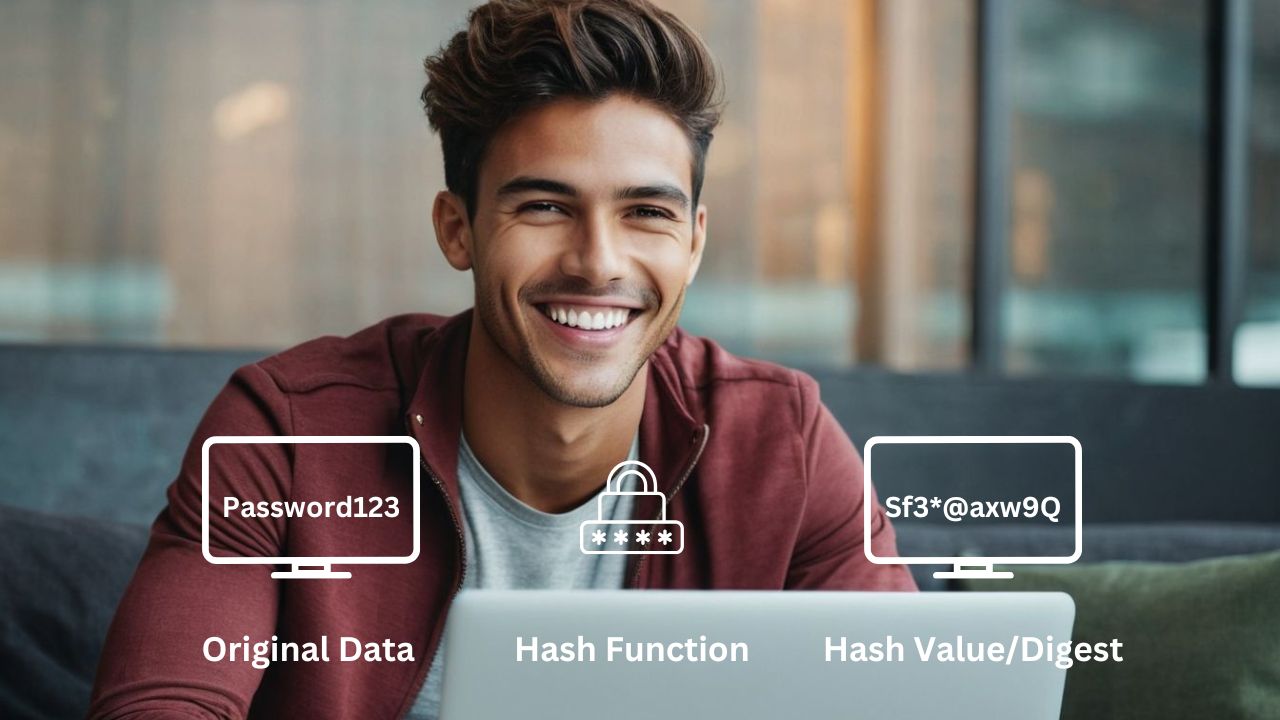
Hashing is the process of scrambling a piece of information or data beyond recognition. Hash functions perform mathematical operations on plain text to produce a fixed-size string of characters, known as the hash value or digest. While this might sound similar to encryption, the key difference is that hashes are designed to be irreversible.
Once data is hashed, it cannot be reversed to its original form through decryption. While some older hashing algorithms have been compromised due to advances in computational power, modern algorithms continue to evolve and remain robust for critical applications such as password storage and identity verification.
Why Is Hashing Necessary?
Password Storage:
When you register on a website, your password undergoes hashing, and the resulting hash value is stored securely on the server. When you log in subsequently, the entered password is hashed again and compared to the stored hash. If they match, access is granted.
The approach ensures that plaintext passwords are never stored, safeguarding user data even if the server’s security is compromised.
Data Integrity:
Hashing also plays a role in verifying data integrity. When someone uploads a file online, the system generates and stores its hash value. Upon downloading the file, users can generate its hash value and compare it with the original. If the values match, it confirms that the file has not undergone any tampering.
Hash Functions
Hash functions serve as cryptographic tools that transform data into fixed-size strings through a sequence of mathematical operations. They split data into uniform blocks based on algorithm specifications. Unlike reversible encryption, hash functions are designed to be irreversible, making it impossible to reconstruct the original data from its hash.
Modern secure algorithms such as the SHA family, with variants like SHA-256 offering a 256-bit digest size, are widely adopted today. The digest generated by a hash function remains consistent for the same input, regardless of how many times the calculation is performed.
Guidelines for Effective Hash Functions
Creating a robust hash function involves adhering to specific guidelines to ensure optimal security. These requirements are crucial for maintaining data integrity and thwarting potential security threats:
- Speed and Security Balance A hash function must balance speed and security. It should be fast enough to handle large amounts of data efficiently but not so fast that it becomes vulnerable to brute-force attacks. Finding this balance is crucial for effective hashing.
- Dependency on Input Bits Each bit of the input should influence the output hash. A small change in the input, even just one character, should produce a completely different hash. This ensures that each piece of data has a unique hash value.
- Prevent Hash Collisions Hash collisions occur when two different inputs produce the same hash value. This is a potential security risk, as it can lead to unauthorized access. Techniques like salting and peppering are used to reduce the chances of hash collisions.
Strengthening Hashes: Salting and Peppering
When dealing with sensitive data such as passwords, ensuring their security goes beyond simple hashing. There are two essential techniques—salting and peppering—that significantly bolster hash security.
Salting
Salting involves adding a random keyword to the end of the input, known as salt. This unique salt value ensures that even if two users have the same password, their hashes will be different.
Storing salts alongside hashed passwords in the database, often in plain text, speeds up login verification. However, this approach poses a security risk: if the server is compromised, both the hashed passwords and salts could be exposed, making brute-force attacks easier. Peppering addresses this vulnerability by adding an extra layer of security.
Peppering
Peppering adds a random string of data to the input, known as a pepper, before hashing it. Unlike salts, peppers are hardcoded into the website’s source code. This uniform addition of a pepper ensures that even if database access is compromised, attackers lack the essential pepper required to decrypt hashed passwords.
How to Create Hashes and Checksums?
If you’re looking to create checksums and hashes using various algorithms, Online-Convert offers a wide range of options to choose from. While it may not cover every available algorithm, it provides a comprehensive selection of hashing algorithms and encryption ciphers.
Follow these steps:
- Visit online-convert.com: Select Hash Generator.
- Choose Your Method:
- Paste Text: Enter the text you wish to convert into a hash or checksum directly into the provided field.
- Upload a File: Select a file from your computer to generate a hash.
- Enter URL: Provide a URL to a file or website from which you want to generate a hash.
- Cloud Services: Access files from cloud services like Dropbox or Google Drive for hashing.
- Convert Your File:
- Once you have input your data or selected a file, click on “START.”
- Hash generator tool will process your request and generate the checksum or hash.
This straightforward process ensures you can quickly and securely create hashes and checksums!
In Conclusion: Hashing
Hashing is essential for securely managing sensitive data like passwords. By converting data into irreversible strings, hashing ensures data protection even in the event of breaches. Techniques like salting and peppering further fortify hash security. Understanding hashing’s mechanics and applications is key to safeguarding our digital assets!