So, you have heard of hashing—a fundamental concept in cybersecurity and data management—but want to understand more? This article will cover why hashing is crucial, its core principles, types of hash functions, important guidelines for algorithm selection, and techniques to enhance hash security.
So, let’s get started!
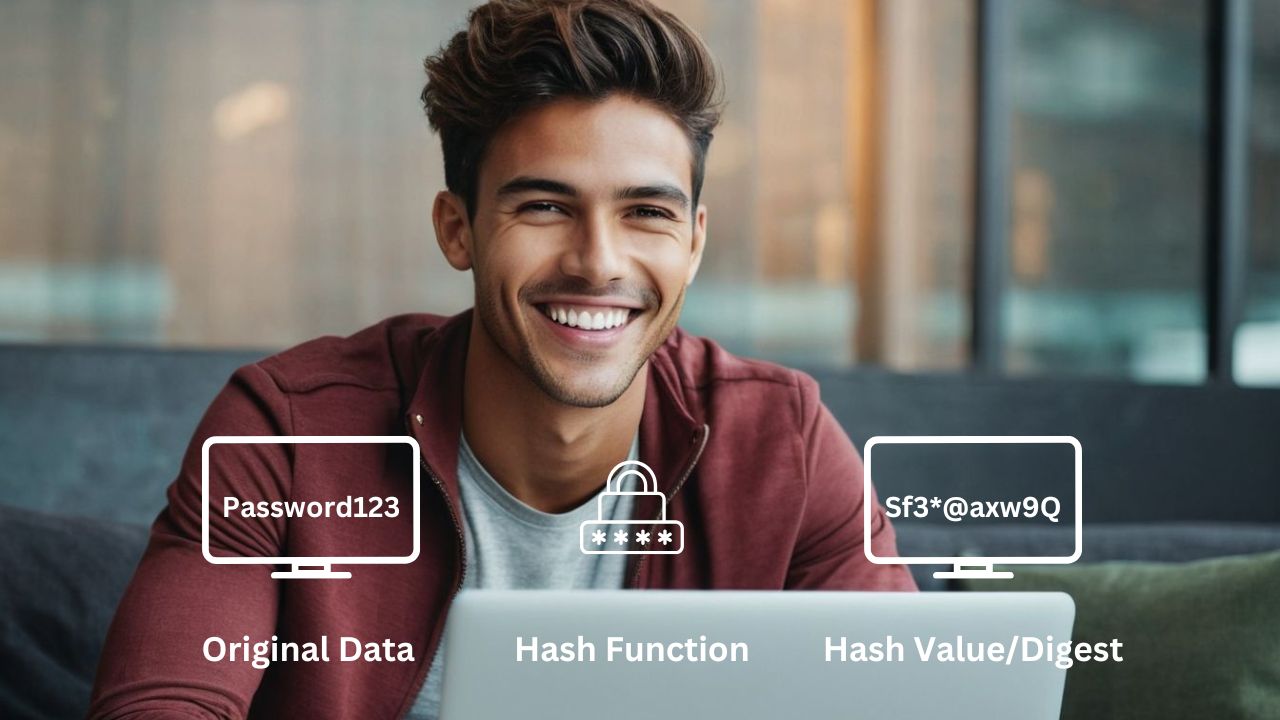
What is Hashing?
Hashing is the process of scrambling a piece of information or data beyond recognition. Hash functions perform mathematical operations on plain text to produce a fixed-size string of characters, known as the hash value or digest.… Read the rest
