
Online-Convert.com is a free online conversion tool. You can convert many different files to more common formats, including audio, video, e-book, document, images and more. You can even convert across categories like text to speech or presentation to video.
However, that is not all you can do on Online-Convert.com! As an additional feature you can create checksums and hashes using different algorithms.
Since we get quite some questions about our hash creation, we decided to create this frequently asked questions (FAQ) entry for you.
Hash Generation FAQs
What Is The Difference: Encoding, Encryption & Hashing
In the past we have written a long and informative article about the difference between these three. You can re-read it here or check out the small summary below:
Encoding, Encryption, and Hashing
| Encoding | Encryption | Hashing | |
| Data Security | Not secure | Secure | Secure |
| Reversibility | Reversible | Reversible | Not Reversible |
Looking at the table above, the difference between the three systems becomes very apparent.
- Encoding should not be used to secure data since the data is easily decoded. As soon as the encoding system is known, the data can be decoded using the very same system.
- Encryption, however, can be used for securing data since it can only be de-crypted with a respective key, even when the encryption method is known.
- Hashing is also a safe method to secure data. However, once hashed the data can not be reversed to its original form again.
What Do I Need A Hash Generator For?
Hashes and checksums are used to create a string of characters out of different data entries. This way, sensitive data can be secured. Furthermore, hashes change their form once the input is altered. These two basic functions can be used for several purposes like:
- Searching in a big database
- Checking downloads & sent/transmitted data
- Comparing passwords without saving the actual password
- Detecting duplicate content or alterations in general
Detailed descriptions of the usages mentioned above can be found here:
Checksum & Hash – What are they and what do I need them for?
What Algorithm Should I Choose?
Online-Convert.com provides a big list of different hashing algorithms and encryption ciphers you can choose from. Of course, it is not an exhaustive list, but it provides a good selection of different systems.
Since listing the pros and cons as well as the advantages of each algorithm or cipher would exceed the span of this article, have a look at this separate article about the advantages and functions of different hash generators:
Different Hash Functions and their Advantages
How Do I Create A Hash/Checksum?
Once you decided on your method, you can start creating checksums from your data. With Online-Convert.com, this is fairly easy.
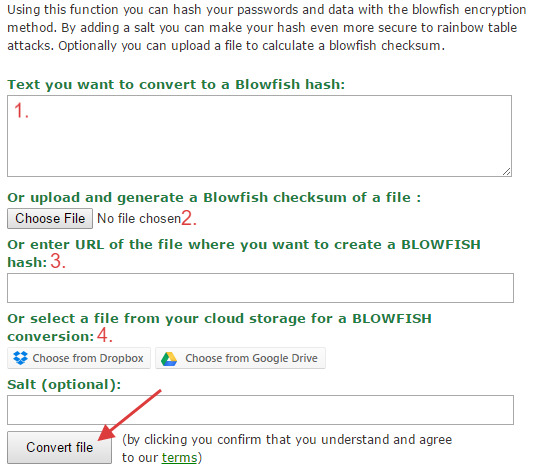
There are four main methods of providing data you want to have hashed or encrypted:
- Paste text you wish to convert into a hash or checksum
- Upload a file
- Enter the URL to a file or website you want to generate a hash from
- Choose a file from a cloud service like Dropbox and Google Drive
Afterwards, click on convert file and wait a little until the checksum is created.
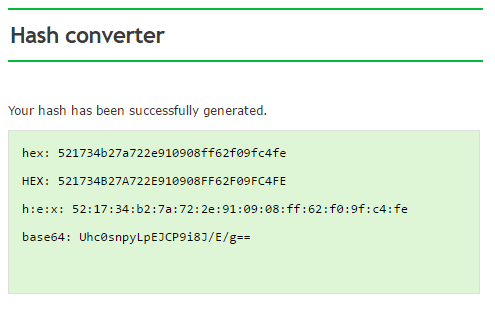
What Else Is There To Know?
As you have probably seen above, there are also optional settings available for the hash generation. Lets have a look at them.
HMAC Hashes:
Some hashes have been generated using a keyed-hash message authentication code (HMAC). In order to provide a correct hash for comparison, the HMAC of the original hashing should be entered.
This is available for the following methods:
Adler32, CRC, Gost, Haval, MD4, MD5, RIPEMD, SHA, Snefru, Tiger, Whirlpool
Salt:
A salt can be used for hash generation to extra-secure the hashes. When added, the salt provides additional security against dictionary and rainbow table attacks.
This is available for:
Blowfish, htpasswd Apache
Rounds:
Some hash functions are able to generate hashes using different rounds. The hashes differ depending on the number of rounds used for the generation. The default value, using Online-Convert.com is 3 rounds, but you can choose 4 or sometimes even 5 rounds as well.
This is available for:
Haval, Tiger
